Ready to talk about your network?
Let us introduce you to the world’s only all-in-one network visibility platform.
Pretty sure you can spot a phishing site in the wild? Try your hand at our Spot the Phish game and see what your score is! Review 5 randomized pairs of side-by-side sites and click on the phish.
With the growing popularity of the dark web for illegal commerce, it’s easy for hackers to purchase phishing kits that can spin up similar to nearly identical copycat websites featuring matching fonts, logos, and images. Popular kits include Kali Linux, Zphisher, and SocialPhish.
If clever character substitutions in URLs don’t fool you, you could still end up on a phishing site through malicious redirects placed on compromised sites. Traffic is redirected from the legitimate site to hacker-controlled replica sites. Machine Learning outsmarts this technique by training models to look at specific phishing features beneath the surface of site presentation.
 Good
Good
 Phishing
Phishing
Did you know hackers can use HTTPS protocol for phishing sites to create a sense of trust and legitimacy for users? Even phishing sites can get the HTTPS certification and secure site padlock icon beside their URL. The padlock does not mean the website is safe, only that the connection is encrypted, but this often creates a false sense of security for users.
Phishing sites can use special characters that human eyes often don’t detect within the URLs. For example, ɑ looks very similar to a, but they are different. Hackers use letters from the Cyrillic alphabet and other foreign languages with nearly identical characters to get you onto their phishing sites.
 Good
Good
 Phishing
Phishing
Hackers can create a pixel-to-pixel identical website. Everything from logos to fonts, even to how the URL is displayed on the page, is intended to mislead targets to enter their credentials on the clone site.
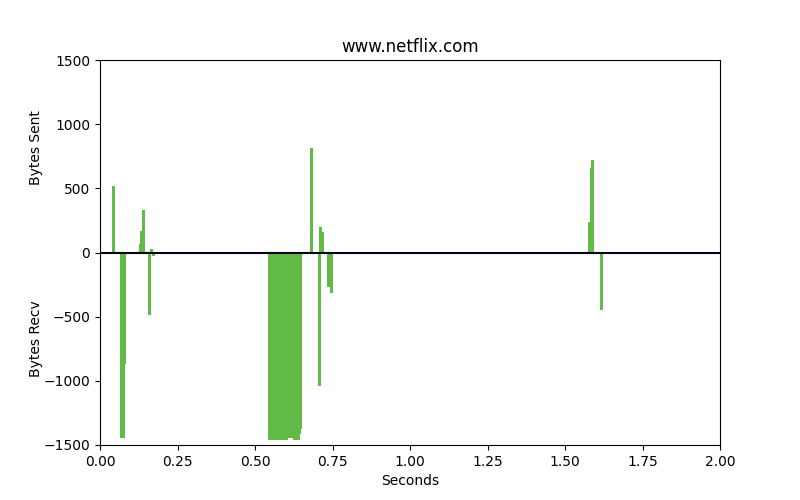
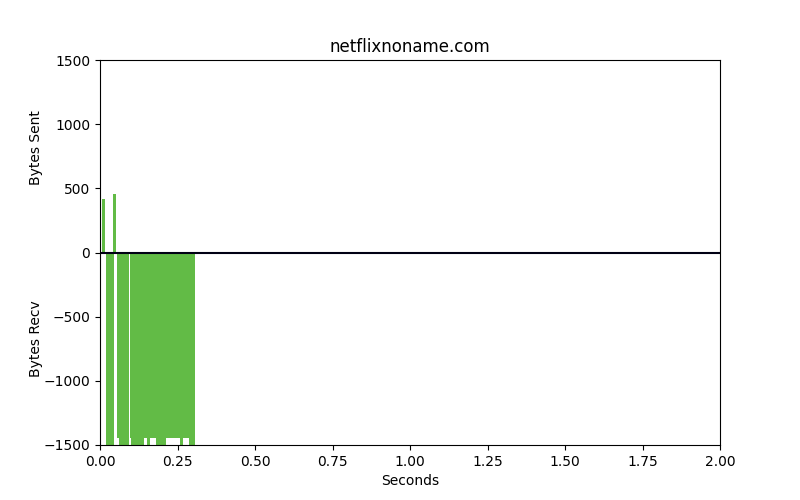
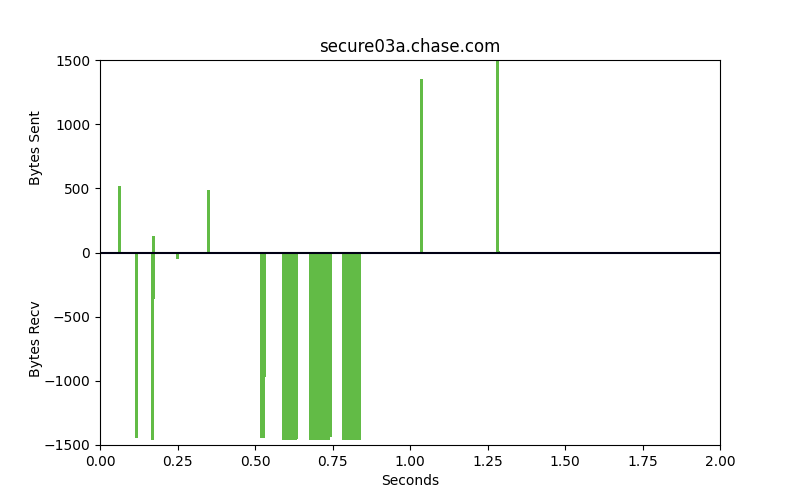
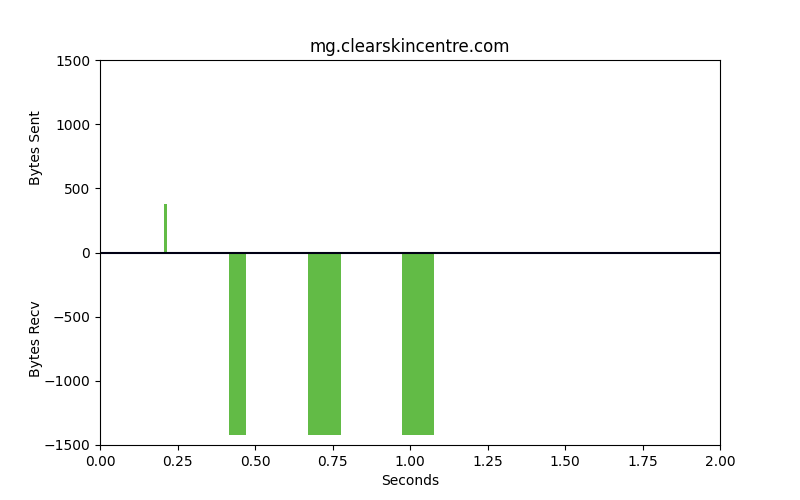
Packet patterns can see what the eye cannot. These two identical-looking websites have distinct packet dynamics. Bytes sent and bytes received over time look very different. We can see overall characteristics frequency in size, the ratio of bytes sent to bytes received, and actual encrypted bytes to evaluate patterns in encryption use and strength of encryption against our ML model.
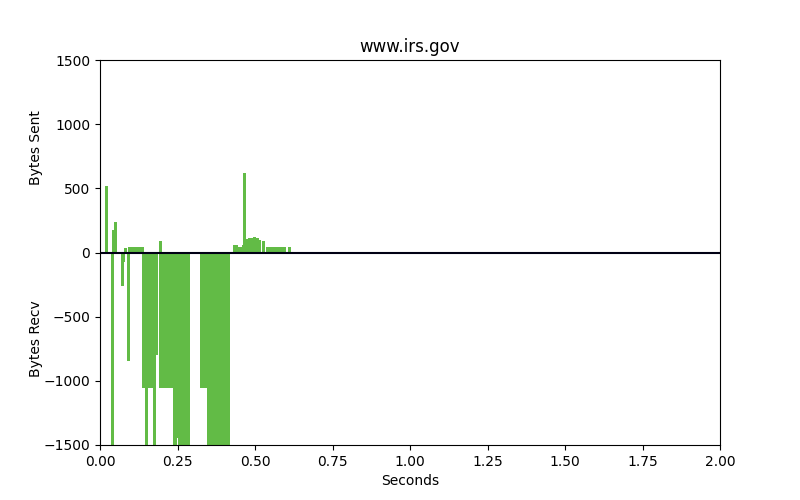 Good
Good
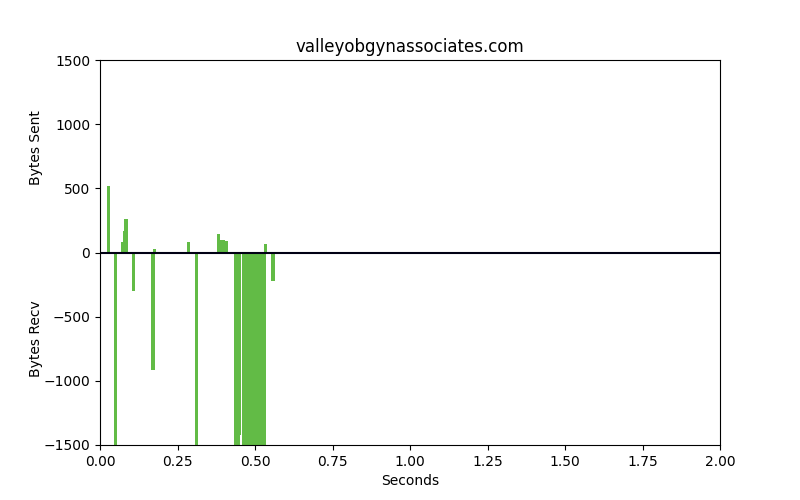 Phishing
Phishing
Hackers often use legitimate-looking domains with lookalike words using similar letter or number combinations to attack you. This is called “Domain Spoofing.”
ThreatEye uses a trained machine learning model that ingests data from thousands of known phishing sites against known legitimate sites to detect any traits that would be exhibited by phishing sites.
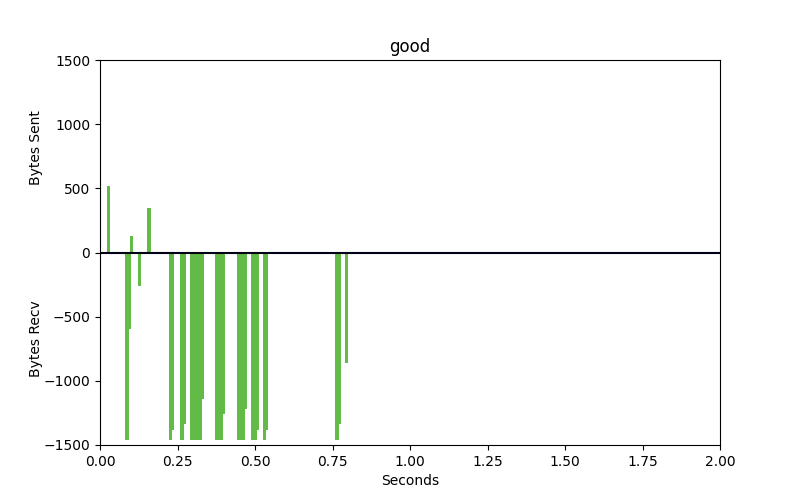 Good
Good
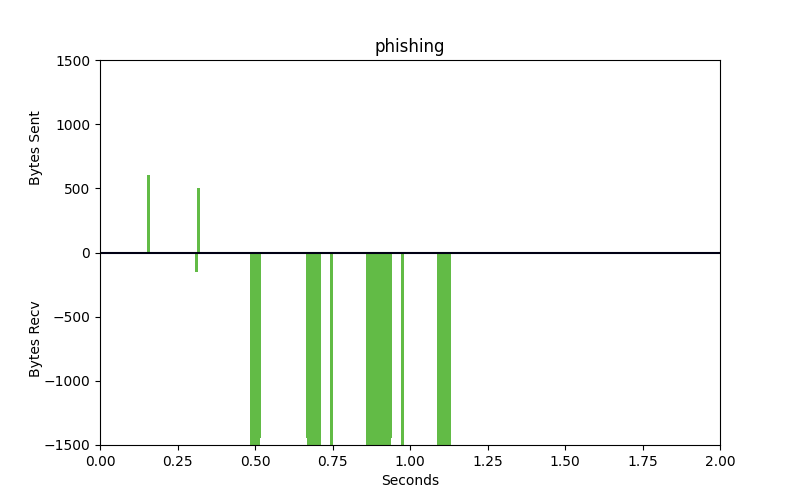 Phishing
Phishing
According to the US Federal Bureau of Investigation, phishing attacks are expected to increase by as much as 400% yearly. The websites most likely to be targeted belong to financial institutions, email and social media platforms, and eCommerce retail stores.
These are very different flows. One is legitimate, the other is malware. The bars that go up are packets that are sent from the client to the server, uploads. The bars going down represent bytes from the server to the client, downloads. The space between the bars represents the interpacket arrival time or how much time is spent between these packets being sent. Legitimate websites typically invest in greater resources and return results with smaller spaces between the bars.
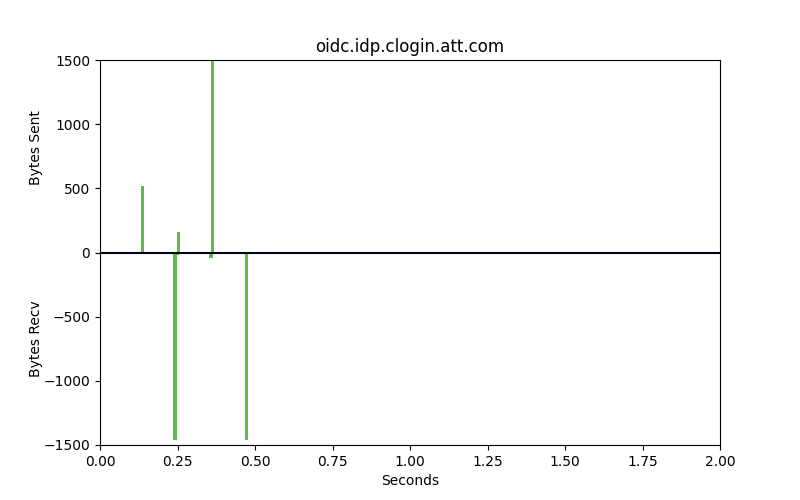 Good
Good
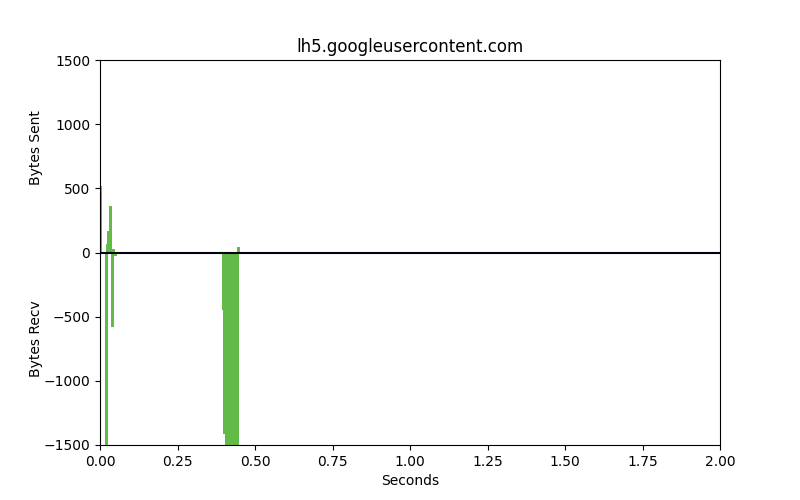 Phishing
Phishing
Don't feel bad. 97% of people cannot identify a phishing scam. That's why we created ThreatEye.
It's a high-risk game where even one wrong guess can spell an organization's ruin. Get an extra set of eyes with ThreatEye.
Are you sure you're a human? You've tied the high score with our machine learning engine ThreatEye but others might not be so lucky. Get a perfect score every time with ThreatEye.
ThreatEye always holds the perfect high score on our Spot the Phish leaderboard. Discover the science behind ThreatEye's phishing detection and why it's built to win every time.
Let us introduce you to the world’s only all-in-one network visibility platform.