
October is National Cybersecurity Awareness Month and the theme, “See Yourself in Cyber,” focuses on how individuals can impact an organization’s security through simple choices. Today we look at phishing indicators and trends that can help you avoid falling for phishing lures.
Awareness of phishing attack strategies will give you an upper hand in spotting their attempts. Understanding how attackers create compelling situations that take advantage of psychology and emotions can also keep you on the outside of their luring attempts.
1 – Understand How Your Emotions Get Exploited
Expressing Urgency or Fear
Look for language that uses consequences and drives deadlines. Terms like “Immediate attention required,” “expiring within 24 hours”, or “Your account is suspended.”
Immigration Deportation
It could be customs officials demanding money or a required fee to avoid immediate deportation.
Account Closure
It often includes a CTA link or button asking you to “update your account now,” leading to the copycat phishing site where entered credentials are stolen.
Student Loans
These can come as phone calls or emails with claims to have a relationship with the US Department of Education and the ability to consolidate your loans for lower payments (for a one-time processing fee).
NOTE: Only the federal government can consolidate loans, and there is no fee. Check with Studentloans.gov or call 1-800-557-7394. The government does not charge a fee for student loan consolidation.
Unknown sign-in that now requires you to verify account information
Did someone from Spain log into your account? Don’t click on the email link to find out – go to the source of the notice by logging in through your browser and checking your account for notices.
Official Data Breach Notification
These notices are intended to alarm users into quickly clicking the provided link to see if their account was breached. Access the account via a known website domain to confirm if a breach has been flagged on your account.
Change of Password Required Immediately
Access the account via a known website domain to confirm if a breach has been flagged on your account.
Fake IT Password Reset Request.
This may look like an innocent reminder for a password reset and include a timeframe like 24 hours. Check where the email comes from and verify the source before moving forward.
Situational Vulnerability
When charities or the government get involved, there is always an opportunity to exploit victims. Here are a few situations we’ve seen successful phishing attacks.
Anticipated federal program contact
- Federal disaster relief
Threat actors pretending to be insurance adjustors charging a considerable upfront cost or a FEMA employee offering to speed up claims and repair processes and offering access to grants and permits with a small upfront fee and some personal information. FEMA does not ask for upfront fees.
- Tax refunds – posing as IRS
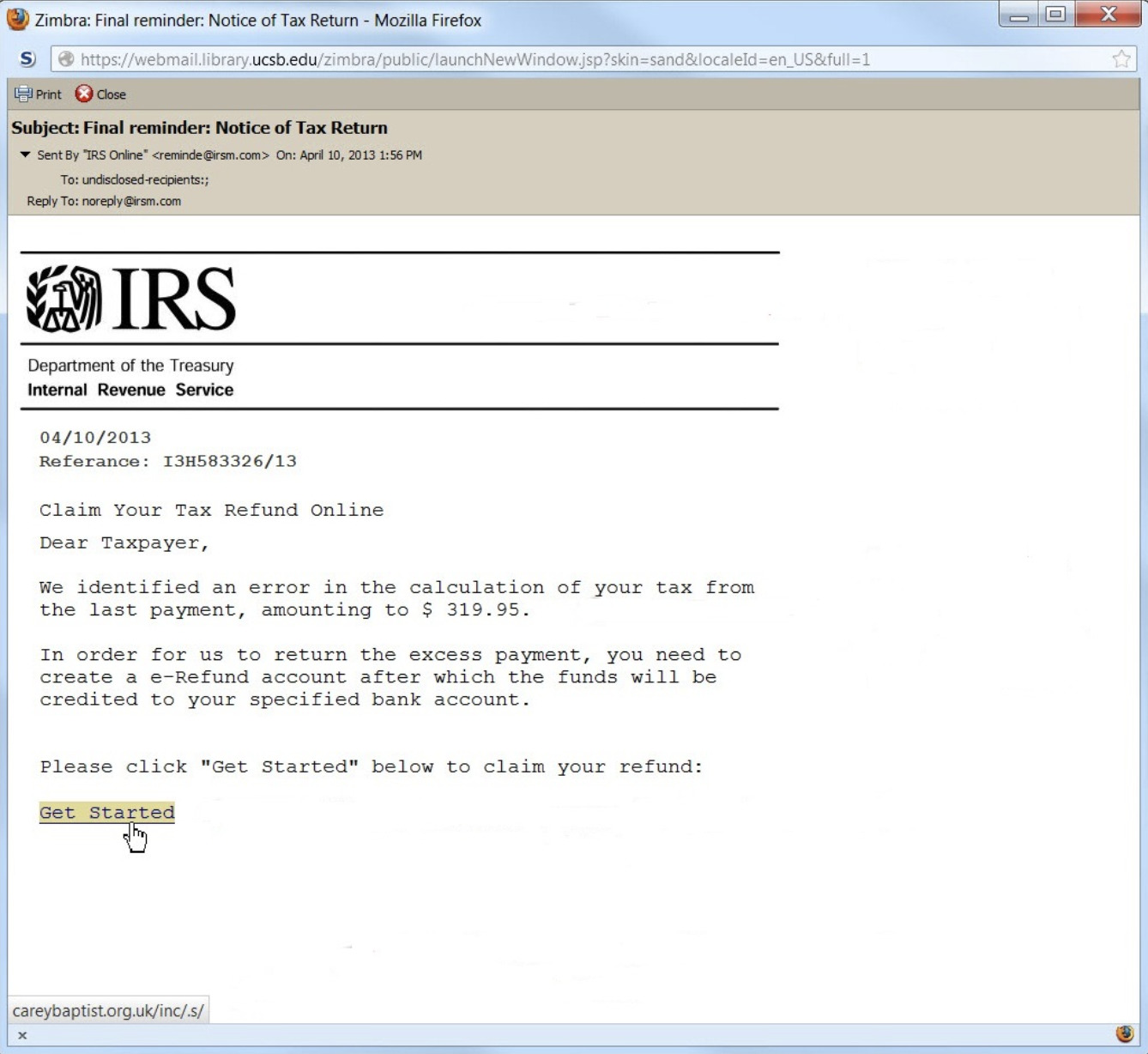
- Social security
They may threaten to suspend your social security number without immediate payment. Social security does not suspend your social security number, and they do not accept payments over the phone, through crypto, or any other means than electronically through Pay.gov or physically by check or money order to an official office
- Small Business or Student Loans
May offer no-cosign or no-credit loans and will request bank account information
Fake charity organizations ( more popular around Christmas time)
- Veterans fundraiser
- Disaster relief – floods, earthquakes, tsunamis
- War in Ukraine victim relief funds
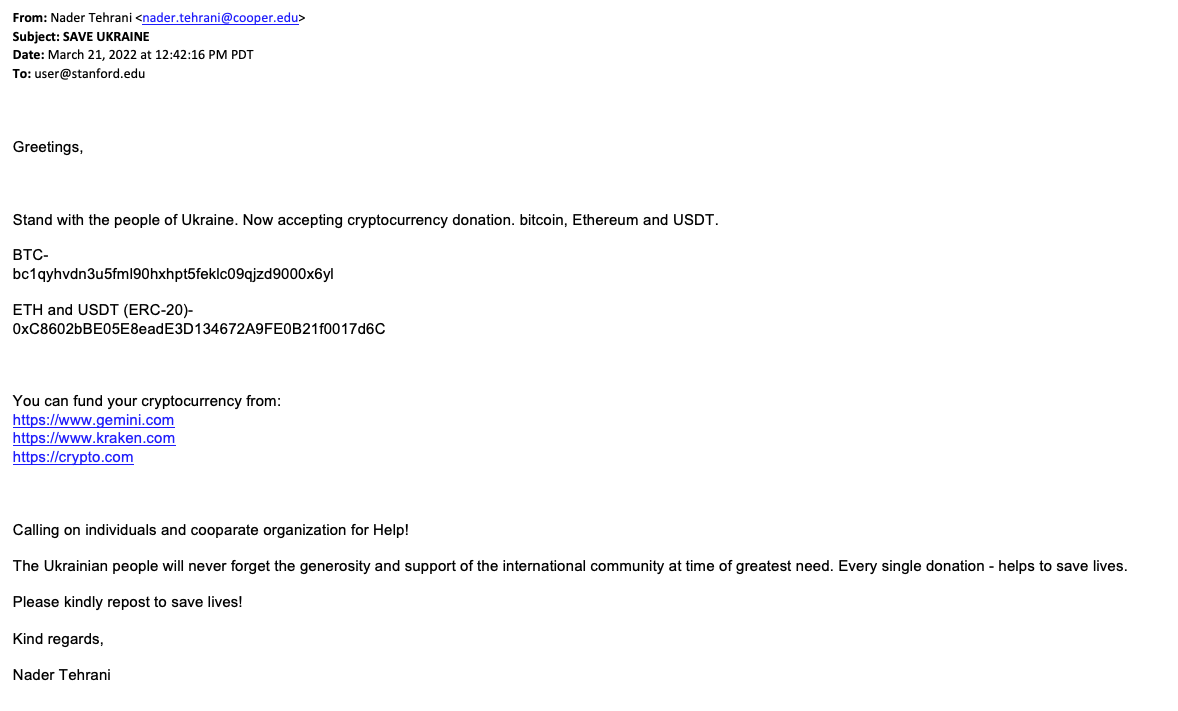
Check out a complete list of accredited charities at give.org.
Using Relationships
These attempts will try to build trust and ultimately ask for money or claim that you (or they) are in legal trouble and create high-pressure situations, like being hospitalized.
- Masquerading as someone from your company or a trusted department like HR
- Important Notice on Your Benefit Eligibility from Human Resources
- Pretending to be someone you know, a distant relative or acquaintance in a pinch
- Romance interest (catphishing) involving long conversations and resulting in requests for money
- NOTE: It’s unlikely you’ll ever meet this person. Anticipate lots of excuses.
The Excitement of Winning
Winning creates excitement and adrenaline and can cause decisions without examination
- Usually, these techniques will require a fee to ship the prize and will capture your credit card information from that transaction, shipping address, name, email phone number, and other data that can be sold in lists on the dark web
- Anytime something of value, like a trip, free SkyMiles, or a new iPhone, is being offered for free via sweepstakes or raffle, it’s a good idea to exercise suspicion
- Look also for claims of inheritance or lottery winnings that require a one-time payment of an admin fee to collect
2 – Be Aware of Common Phishing Techniques
While phishing emails are the most popular platform of abuse, several techniques and platforms are used to attack. Here are a few of the most common, so you know what to look for.
Phishing Emails
This is the most popular and most effective platform used by phishing attackers. The classic OG phishing scam was the Nigerian prince’s email asking for enough money to unlock his accounts and promising handsome return rewards for your assistance.
Here are a few categories of modern email phishing attacks:
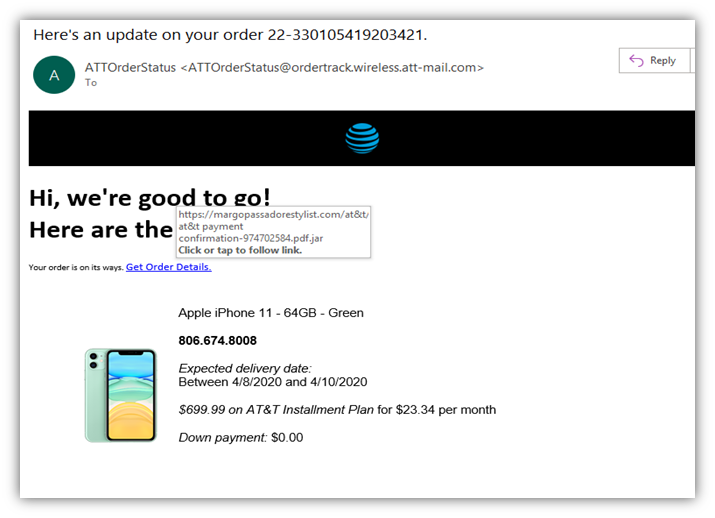
HTTP Phishing
Links to a phishing site, claiming you need to reauthenticate or log back in an account alert, or an order confirmation including a link to a phishing site – Don’t Click on hyperlinks in emails. Hover over the link to see the URL and type the URL into the domain, or google search it. The hyperlink could be spoofed to send you to a fake phishing site.
Spear Phishing
Targets an individual specifically using information grabbed off your linked or social pages. They know your name and other information about you to ingratiate trust.
Whale Phishing
Whale phishing targets C-level executives in the company for specific sensitive data.
Angler Phishing
This technique uses a fake social media post to trick you into giving login credentials, ex: you’ve been tagged in a photo, or this user commented, “wow, I was surprised to see you in this.” A recent rash of angler phishing emails have told targets that they violated Instagram’s copyright laws and that their account will be deleted in 24 hours. The email includes a link to click for account verification if you believe Instagram is mistaken.
Malware Phishing
Phishing emails that contain a trustworthy-looking attachment file, a word doc, or a pdf that contains malware. This could be a company announcement, a copy of insurance cards, a resume, a financial statement, etc.
Phishing Websites
Victims usually arrive at phishing sites by redirects or links from email or text spoofing. But they can also trick search engines with nearly spelled sites that catch people typing in the business name too quickly and design that look similar to the legitimate site. These copycat sites are built by hackers or created from kits purchased on the dark web.
Phishing Pop-ups
These popups on your browser or computer screen
- Your antivirus software has expired
- Claim your free iPhone
- You qualify for a free AppleCare renewal
Word to the wise, nothing good can come from pop-ups.

Via Phone Call or Text
This is sometimes called vishing or smishing. Here are the typical offenders:
- Someone pretending to be a relative or someone who knows you
- Someone pretending to be the embassy calling and needing money for a relative
- A call about a car warranty or recall
- A voicemail about student loans
- Any phone call you did not initiate the contact, but they asked for personal information over the phone
Phishing via Fake WiFi
This is called “Evil Twin” phishing and happens in places with public WiFi access. The “evil twin” is a duplicate access point modeled after the legitimate hotspot. For example, you may find this at coffee shops, libraries, hotels, or the airport, and more than one wifi network claims to offer this legitimate service.
PRO TIP: If you’re experiencing a slow connection, it could indicate your traffic is routed to a malicious network.
- When using public WiFi, avoid accessing your bank or logging into private work environments.
- Using a VPN tunnel is another must-have practice. It encrypts your data, so even if, on an evil twin network, your keystrokes are protected from hacker tracking attempts.
Here are some uncomfortable stats, the Identity Theft Resource Center found that 23% of people polled admit to making credit-card purchases over free Wi-Fi hotspots. The Harris Poll found that 26% of US adults check their bank accounts on free Wi-Fi hotspots.
57% of those polled in an ITRC survey admit to logging into work-related platforms over these free hotspots.
3 – Follow Best Practices in Cyber Hygiene
When interacting with and opening emails, the behavior must be cautious. Here are a few of our top tips
- Look for a discrepancy in display names and check the mail address before opening a message. Once opened cross check the information in the signature with an online search.
- Never click on hyperlinks in emails. Copy the link, paste it into the search and see what comes up. When in doubt, visit institutions through their home page.
- Use a password manager that can log you into legitimate sites. Password managers will not work on realistic phishing site models and can tell the difference.
- If you have any suspicion, confirm the message source
- If claiming to be internal, cross-check with the employee mentioned on your company messaging platform.
- If external, check the information in the signature against the company listed in a Google search.
If it doesn’t match up, let your IT team know of the attack attempt by taking a screenshot of the message, reporting the message source, and deleting the email.
- Do Not Reply to Unknown Senders
Be Cautious of the following:
- Redirect buttons or hyperlinks within the email
- Do not click on hyperlinks or redirect buttons- they can pose as several things, including unsubscribe buttons (which you can bypass by marking the email as spam within your email settings).
- Hover over links, and type them in directly – read carefully for other languages using characters similar to familiar letters or flipped letters that can catch the casual reader off guard ex: PayPal or Pyapal. Paste these into google search first and see if any spam alerts come up.
- A request to enable macros in a word document or download something
- ex: bank statement, resume, shipping tracking
- A request to update a password
- Social Media connection request
- Unknown senders or phone numbers
- A request to update account information
About LiveAction
No matter how many times people are told to practice good cyber hygiene and take security precautions in their daily online lives, some simply can’t be bothered.
The Ponemon Institute found that even with people that know better like IT security practioners, only 33% use some form of two-factor or multi-factor authentication in their personal lives. Don’t leave an organization’s security in the hands of the individuals.
LiveAction offers industry-leading network performance monitoring solutions designed to meet the unique needs of large organizations with complex networking environments. Our solutions provide deep visibility, real-time analytics, and comprehensive security integration, ensuring robust network performance and compliance. For more information, visit www.LiveAction.com

