
This year’s National Cyber Security Awareness Month highlights action steps individuals can take to make a difference in cyber security. One of the four items CISA calls out is passwords, specifically recommending password managers.
Password managers are an underutilized, easy-to-implement tool that can have a ripple effect in stronger security across an organization. They also tackle a major human flaw head-on, apathy. Anything requiring effort is a hard sell to the public – this applies to everything in life, and password management is no exception. This alarming statistic from a national Harris Poll underlines how unwilling people are to exert any additional effort, even when they know better.
Only (45%) of people would change their password to an online account even after being informaed of a data breach.
Password managers are one of the best hopes an organization or individual has for changing risky convenience-prioritized behavior.
What is a Password Manager?
Password managers are encrypted software applications that keeps track of your passwords for different systems and devices. The user must remember only one over-arching password to unlock access to the manager which securely stores all other passwords.
Why use a Password Manager?
Less to Remember
A password manager saves the password, so you longer have to rely on memory or the piece of paper you have buried somewhere on your desk. Password managers also have the secondary benefit of making end-users less likely to reuse their passwords.
Faster Login Access
Once you’re signed in to your password manager, it will auto-fill login information for you to sites you’ve logged into before. This saves the time of entering and mistyping information in the login screen.
Saves Other Information
Password managers can save addresses, emails, credit cards, and other sensitive information.
Better Quality Passwords
Many free password manager services include a password auditing feature that tells you if your password is weak, ok or decent.
 Brute Force Attacks
Brute Force Attacks
Hackers are able to crack passwords faster than ever before with key-stroke logging software, purchased already-breached credential lists off the darkweb, scanning for default system passwords and password spraying for the most commonly used passwords.
How many characters is your password? Follow the chart to the left to see how long your password could withstand a brute force attack.
Tips on making a strong password
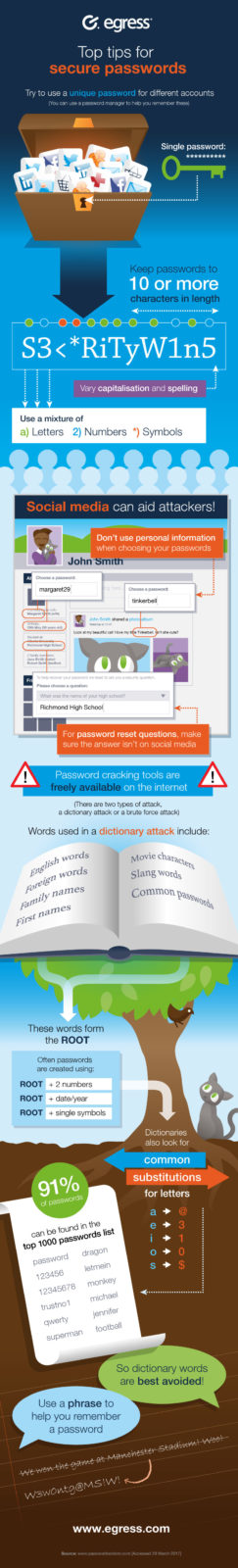
Password managers give you the option of auto-generated strong passwords, but if you choose to make your own follow these tips.
- Don’t use variations of the same password or just add a different number onto the end sequentially. This is not a unique password.
- Don’t make passwords based on personal information
- names of your children or pets
- FUN FACT: Did you know Eva and Alex are the most commonly featured names in passwords?
- addresses and street names
- important dates from your life ( birthday, anniversary etc.)
- names of your children or pets
- Don’t make passwords based on famous sayings, phrases, or lyrics
- Do use acronyms and letters that don’t spell words that can be found in the dictionary
- Use capitalization, numbers, and punctuation
6 Free Password Managers to check out
These password managers each have premium versions that can be upgraded to for additional features.
LastPass – unlimited logins for unlimited devices and syncs between devices, password auditing
Avira – unlimited logins for unlimited devices and syncs between devices and unlimited password storage but limited password auditing
Roboform – unlimited logins for one device with password auditing
Dashlane – unlimited logins for one device, but you can share an unlimited number of passwords with family, colleagues, etc., and will audit passwords for you
Sticky Password – unlimited logins, unlimited devices, and biometric authentication with fingerprint or face scan does not sync between devices and password auditing.
Bitwarden – opensource free, unlimited logins, unlimited devices but less user friendly
About LiveAction
No matter how many times people are told to practice good cyber hygiene and take security precautions in their daily online lives, some simply can’t be bothered.
The Ponemon Institute found that even with people that know better like IT security practioners, only 33% use some form of two-factor or multi-factor authentication in their personal lives. Don’t leave an organization’s security in the hands of the individuals. ThreatEye identifies an attacker’s presence through all stages of the MITRE ATT&CK sequence for early detection and intervention if they make it past the password. Talk to us about your security needs and learn more about how to put up a safety net around your organization today.

